
What is TLS?
Discover the basics of Transport Layer Security (TLS) protocols and learn how they can help your organization.
What is TLS?
TLS stands for Transport Layer Security. In short, it’s a cryptographic protocol that upholds privacy and data integrity for web-based communications, such as internet browsing, webmail, and video conferencing. More simply, it uses encryption algorithms to mitigate the risk of hackers hijacking connections between online devices and applications.
As a security protocol, TLS gets its name from the Open Systems Interconnection (OSI) model. The OSI model is a conceptual framework for how network communication works, breaking it down into seven layers. TLS primarily operates at the transport layer, enabling secure communication between two endpoints. That said, it also secures application-layer protocols like HTTP (Hypertext Transfer Protocol) for web browsing and SMTP (Simple Mail Transfer Protocol) for email, among others.
Overall, the TLS protocol has three primary functions:
- Encryption: TLS encryption hides sensitive data as it’s being transferred, protecting it from unauthorized access. In other words, it establishes a secure connection, allowing two or more parties to exchange information safely.
- Authentication: It also ensures that all parties involved in the transaction are who they claim to be. For example, in the case of internet browsing, it confirms the authenticity of a website or web server for a browser.
- Integrity: TLS verifies that data hasn’t been forged or tampered with by third parties and that all information reaches its destination as intended.
What is SSL?
SSL stands for Secure Socket Layer — the predecessor to Transport Layer Security. Like TLS, it’s an internet security protocol that authenticates websites and enables secure communication through an encrypted connection.
A computer services company called Netscape developed the original SSL protocol in 1995. However, it never released this version to the public due to glaring security flaws. After two subsequent iterations, the Internet Engineering Task Force (IETF) proposed the first TLS protocol in 1999.
The IETF originally developed TLS 1.0 as SSL 3.1. Although the company rebranded to avoid issues with Netscape, many in the industry still refer to TLS by its former name. You may even see combinations of the two, such as references to TLS/SSL encryption.
What’s the difference between TLS and SSL?
Despite the confusion, the two protocols are very different for several significant reasons:
- Cipher suites: TLS offers a broader range of cipher suites compared to Secure Socket Layer. In short, a cipher suite is a set of algorithms for use in establishing secure communications. With more flexibility, TLS allows users to select the suite that best matches their security requirements and preferences.
- Security: TLS encryption is much stronger than SSL encryption, and each version has improved upon the last. TLS 1.3, for example, removed older cryptographic algorithms and insecure features and introduced perfect forward secrecy. In essence, perfect forward secrecy is a feature of cryptographic systems where each session key is unique and derived independently, ensuring that the compromise of one key doesn’t jeopardize past or future communications.
- Compatibility: TLS is designed to be backward compatible with SSL. This allows systems using older SSL versions to communicate with those using newer TLS protocols.
In truth, all versions of the SSL protocol have been deprecated for years, meaning they no longer provide adequate protection. By contrast, TLS is now the internet’s default encryption protocol. In fact, the National Institute of Standards and Technology (NIST) requires all government TLS servers and clients to support TLS 1.2 and recommends agencies adopt TLS 1.3 in the near future.
Why use the TLS protocol?
TLS encryption is primarily for protecting web applications and websites from data breaches and other attacks. Without the TLS protocol, unknown third parties could easily intercept and read sensitive data such as login credentials, credit card details, and personal information. Enabling client and web applications to support TLS ensures that data transmitted between them is encrypted with secure algorithms and unreadable by unauthorized users.
Benefits of Transport Layer Security
TLS is an important asset for numerous use cases, such as:
- Enhancing security: With an encrypted TLS connection, you can prevent hackers from eavesdropping, tampering with, or intercepting your sensitive data.
- Improving authentication: TLS provides mechanisms for verifying the identities of both the client and server involved in a transaction. This helps prevent man-in-the-middle attacks, ensuring the client is communicating with a legitimate server and vice versa.
- Building customer trust: Using a TLS connection will provide users assurance their browsing session is fully protected and private. This helps customers feel comfortable sharing their personal information or payment details when opening a new account or making an online purchase.
- Boosting search engine optimization (SEO): Google factors website security into its search engine algorithms. In turn, TLS protocols not only protect users, but also improve your business’s visibility on the results page.
How does TLS encryption work?
TLS establishes a secure connection between a client device, such as a computer or mobile phone, and a web server. Before encrypting the session, it first authenticates the connection. In other words, it ensures the web server is legitimate and not an imposter attempting to steal sensitive data.
This process — known as the “TLS handshake protocol” — begins when the client sends an initial message to the destination server. The server responds with information proving its authenticity, and once both parties have been verified, they conduct a key exchange. In brief, this establishes an encrypted TLS connection, allowing secure communication between the two.
None of this would be possible without three underlying components: cryptography, digital certificates, and public key infrastructure (PKI). Let’s break each of these down one by one.
Cryptography: Symmetric and asymmetric encryption
In simple terms, cryptography is the art of securing communication and rendering it unreadable to third parties. Encryption is an essential aspect of this process, which uses a cryptographic algorithm to transform plaintext data into ciphertext, thereby obscuring the information.
Cryptography also relies on digital assets called “keys,” which are like a secret tool for encrypting and decrypting communications. A public key is known to everyone and is used to encrypt the data, whereas a private key is known to only one party and is responsible for decryption.
Transport layer security uses two different types of key-based encryption techniques:
- Symmetric encryption, also known as symmetric cryptography, uses the same key for both encrypting and decrypting data.
- Asymmetric encryption uses both a public key and private key. Without both, you can’t unscramble the encrypted data.
Although symmetric encryption is often more efficient, it’s risky to put your trust in just one key. The advantage of asymmetric encryption is that it mathematically links its two keys together, thereby making it more difficult for bad actors to crack the code.
Digital certificates
A digital certificate is an electronic file that certifies the ownership of a public key. There are many different types for various use cases, such as code signing, document signing, email, and more.
Web browsers use a TLS certificate to identify and establish a secure connection between a client and server. Each one is uniquely associated with a specific domain or entity, acting as a type of digital identification card. Therefore, you can think of a TLS certificate as an authentication mechanism.
When the client initiates a connection to the server, the server sends its digital certificate, which contains details about:
- The domain name and owner
- Which TLS version it's using
- The certificate’s issue and expiration dates
- The public key
- Its issuing certificate authority (CA) and digital signature
Once verified, both parties generate a shared secret key. This key is then used to compute a message authentication code (MAC) for each message exchanged during the handshake. By comparing the MACs, the client and server confirm that the messages have not been altered in transit, further solidifying the authentication process.
Public key infrastructure (PKI)
Public key infrastructure refers to the roles, policies, technologies, and procedures that create, manage, store, distribute, and revoke digital certificates. Simply put, PKI is the system that binds public keys to their respective identities, whether that be a person, domain, or organization.
Critically, organizations can only obtain a TLS certificate from a recognized certificate authority (CA), such as Entrust. CAs are trusted entities responsible for verifying the requestor’s identity, issuing digital certificates, and digitally signing them using their private keys.
This digital signature serves as cryptographic proof of authenticity and integrity. Moreover, it allows recipients, such as web browsers, to verify the certificate’s validity by decrypting the signature using the CA's public key, which is widely distributed and pre-installed in trusted root stores.
Steps in the TLS handshake protocol
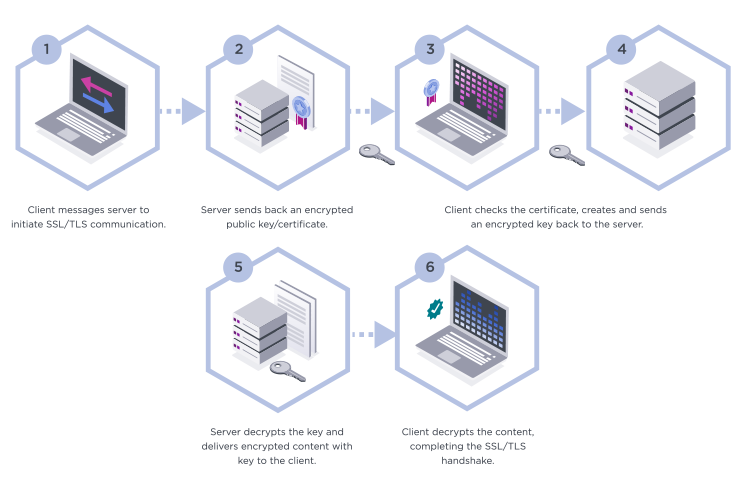
TLS handshakes are a series of messages exchanged by a client and server. The exact steps in the process vary depending on the cryptographic algorithm in use and what cipher suites each party supports. However, regardless of these factors, all TLS handshakes use asymmetric encryption — but not all use symmetric cryptography. In other words, they don’t always use the private key to generate a session key.
Generally, most handshakes will follow these basic steps:
- The client device sends a “Client Hello” message to the web server, including information about which TLS protocol and cipher suite it supports.
- The server responds with a “Server Hello” message. This includes its corresponding TLS certificate, which contains its public key.
- To verify its authenticity, the client checks the server’s TLS certificate with the certificate authority that issued it. This confirms the server is what it claims to be, and that it's operated by the actual domain owner.
- Once verified, the client generates a pre-master secret key — also known as the session key.
- The web server decrypts the session key with its own private key.
- Finally, with the key exchange complete, both parties have a secure connection.
How does TLS impact web application performance?
The newest TLS versions have almost no impact on web applications whatsoever. Although the TLS handshake protocol may seem time-consuming and complex, it actually happens within seconds.
To ensure smooth performance, some technologies mitigate latency, such as TLS False Start. This allows the server and client to transmit data before the handshake is complete. Other options, like TLS Session Resumption, allow the parties to use an abbreviated handshake if they’ve previously communicated.
What is certificate management?
Certificate management is the process whereby digital certificates are generated, stored, protected, transferred, used, and revoked. It includes all of the policies, technologies, and procedures required to manage the lifecycle of digital certificates.
Why does it matter? Because it ensures cryptographic assets are always secure. Poor certificate management practices, such as expired or compromised certificates, can lead to data breaches, man-in-the-middle attacks, or service disruptions.
Luckily, with Entrust, you can simplify the effort from top to bottom. Our solutions include Entrust Certificate Services Platform, a complete management platform for all your digital certificates. It makes oversight easy and intuitive, allowing you to manage the entire lifecycle across multiple CAs from one pane of glass.
How to obtain a TLS certificate
Acquiring a TLS certificate is a straightforward process. Once you know what type of certificate you need, you simply have to submit a Certificate Signing Request to an authorized CA.
At Entrust, we provide flexible and convenient access to a wide range of TLS/SSL certificates, enabling you to make the best choice for your organization. We’re a founding member of the Certificate Authority Security Council and the CA/Browser Forum, which means we’re at the forefront of the industry regarding cryptography.
